Last week at DVCon we had a very interesting Birds-of-a-Feather meeting on Mar 1st evening. Panelists included Tom Anderson from Cadence, Yunshan Zhu from NextOp and Adnan Hamid from Breker Systems.
It was moderated by Srinivasan Venkataramanan from CVC. See pre-BoF invite/details at:
http://www.cvcblr.com/blog/?p=272
The theme of this panel was “Verification Closure” – given that 2011 DVCon marked the birth/release of UVM standard for developing reusable, inter-operable VIPs, it was a perfect fit for a group of technocrats to explore what is beyond UVM. We had some very interesting discussions and here are some excerpts. If you feel I missed some discussion topic or have any comment on this, feel free to blog it here!
To start with, Rick Nordin of Breker Systems introduced the panel topic and the moderator.
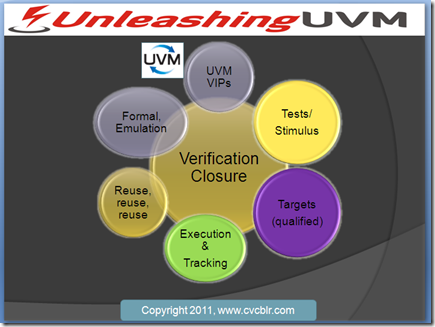
Srini (www.linkedin.com/in/svenka3) presented single slide setting the stage for the panelists and had the honor of introducing the esteemed panelists of the evening: Tom, Yunshan & Adnan.
Here is the slide from Srini:
Basically – we have the UVM now, how do we leverage and verify a complex SoC with it – what are the pieces of the puzzle involved beyond UVM itself? At broad level here are the key pieces:
- Tests/Stimulus – co-ordinated across several UVM VIPs/interfaces – this is far beyond regular SystemVerilog constraints, UVM sequences. Sure UVM’s virtual sequences can help, but with lot of coding and very little reuse from block to SoC level, see http://www.cvcblr.com/blog/?p=272 for some example.
- Targets/coverage goals – not just “code coverage” or “cross every possible input to every possible output” – rather “qualified”, identified and possibly filtered as per existing simulation runs – all automatic
- A robust platform to do the execution, track it in an executable plan and measure the progress
Tom presented first with Cadence’s solution of automated constraint automation, vPlan and integrating adjacent technologies such as Formal, Emulation etc. He was as grand as ever in his vision and covered a whole lot in 1-slide indeed! Pircked it from Tom’s parallel blog on this topic: http://www.cadence.com/Community/blogs/fv/archive/2011/03/11/a-modest-proposal-using-formal-to-close-coverage-gaps.aspx
Then Yunshan presented how to automatically identify qualified coverage targets based on RTL + existing simulation run through NextOp’s Assertion Synthesis. This has caught lot of users excited about this technology and the emerging customer reports from companies like Altera (at deepchip.com) is only making the case more stronger! Here is a quick snapshot of what NextOp brings to the table in this space (from: http://www.nextopsoftware.com/Te_AssertionBasedVerification.html).
Yunshan also presented on how this fits nicely to today’s existing flows and extends the scope for formal/emulation on demand basis. This is extremely beneficial as the audience got to see that NextOp doesn’t really change the flow, rather fitst nicely to any existing flow and brings in value instantly.
Then it was Adnan’s turn to present his views and he started with a BANG! showing how “Model based stimulus-check-cover” generation helps in achieving Verification Closure. In his terms the “testcase generation” is incomplete if it talks “only” about the stimulus – instead it should capture the “stimulus, expect/checker and a coverage model” all in one. A grand idea in plan, call Breker to see how to make it true on your designs!
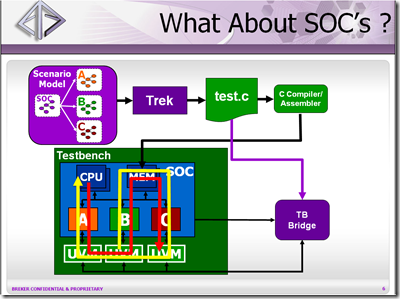
Then Adnan moved on to addressing the SoC level challenges in developing, C based tests with all desired bells-n-whistles such as:
- Reuse of IP level scenarios/graphs
- Automated C test generation
- Heavy memory coherency and
- Debug of such scenarios as-if it is plain SW code (via ubiquitous printf)
Perhaps too much to absorb in 10-minutes, but that’s why they had a booth at DVCon exhibit :-)
Then we had an exciting set of audience questions ranging from “explicit goals to hidden targets” (an interesting attendee posted it by taking examples from Hindu mythological characters such as Ravana & Indra – I will try and cover that in a separate blog on that for pleasure, if not anything else..). A quick summary of that question:
I am clear of an explicit goal to be hit by my SoC env (though it is not trivial to
hit it through simple set of “constrained random sequences” running on their
own, need a great deal of co-ordination).
But what about those “hidden/invisible” targets that are deeply buried inside
my huge RTL code base?
Ans: This is where "Assertion Synthesis” neatly plugs-in – given a set of simulation results, it goes into selected set of blocks/IPs, analyzes it and reports “quality properties” that the design + simulation exhibits. Now the user (typically the block owner) reviews those properties and marks these as assertions or cover holes. Sure there is work – but a targeted set of properties on potentially unstable/suspicious blocks/IPs with automated pruning of “redundant” stuff is a BIG deal indeed. Talk to www.nextopsoftware.com for more!
Some of the attendees:
There were some excited/over heated arguments about temporal properties vs. white-box ones, especially from Vibarajan (http://www.linkedin.com/pub/vibarajan-viswanathan/3/568/343P). The fact is existing System Verilog constructs do a great deal of work for block level/IP level properties, but they fail to deliver at SoC level of abstraction involving class based transaction level behaviors. Sure one can do lot of code around behavioral checkers/scoreboards (and as my good friend Nitin puts it – aren’t you trying to use wrong feature for wrong problem? – I respectfully disagree on this).
Another interesting discussion was around reach-ability of various cover goals. The panel seemed to have the best answers given the abundence of talent/experience on the panelists. Tom explained how formal analysis can either reach them – even if they are hard to reach via regular constrained random generation. Tom also pitched in the role of “unreacahbility analysis” as some of the goals might be just NO-GO given the design constraints/logic and it is very hard to identify them manually. When it comes to higher level, system level scenarios there is this new Graph based scenario models that can literally “mind-map” verification intent thereby letting users “begin-with-end” in mind. You need to listen to Adnan to believe it, or better yet evaluate their flow to benefit from it!
Photos from this BoF courtesy Joe Hupcey are at: http://www.flickr.com/photos/24605532@N08/sets/72157626233541664/with/5513590114/
If you have any more comments/questions to the panel, feel free to add them here in this blog (http://www.cvcblr.com/blog/?p=319) as comments, I will try and get the panelists respond.








No comments:
Post a Comment